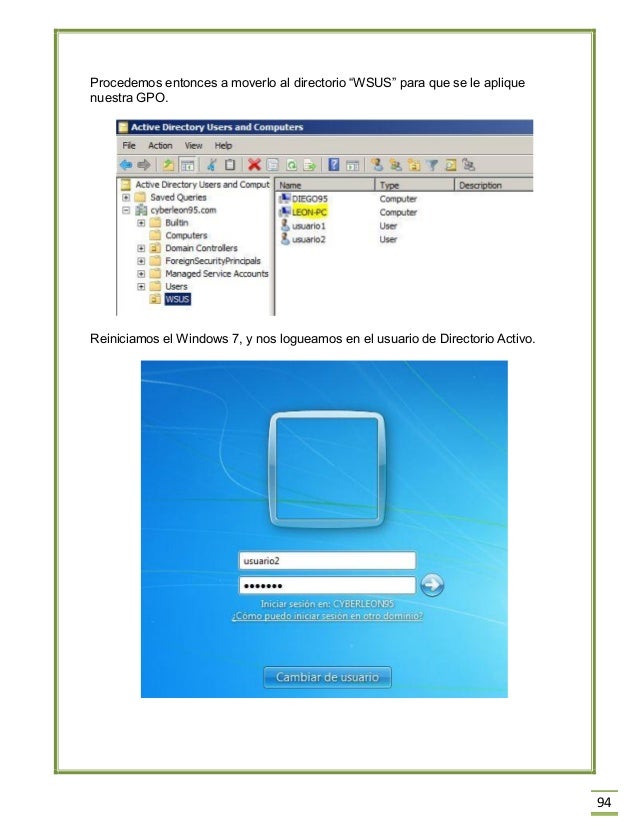
Microsoft fax connector configuration guide. Read online or download PDF. FaxBack Connector for Microsoft Fax - Configuration Guide For Windows Server 2008 R2 User Manual Manuals Directory ManualsDir.com - online owner manuals library. It is not recommended to perform inplace upgrade from Windows Server 2003 or Windows Server 2008 to Windows Server 2008 R2, because in some cases files and registry are overwritten unexpectedly. If you want to use Windows Server 2008 R2, please read this manual and back up necessary data prior to the.
Apr 06, 2013 As I start this blog entry, it’s been nearly 8 months since I created my last self-study guide. For those of you following this blog, I apologize for the long gap. All I can say is that the requirements of work and life, coupled with a mountain of. Apr 16, 2018 Describes an issue in which after you upgrade to Windows Server 2008 R2 you cannot use the 'runas' command, the 'Run as Administrator' option, or the 'Run as a different user' option. Provides some workarounds. Search Microsoft Windows 2008 Server R2 Documentation Find articles, manuals and more to help support your product. What can we help you to find. Submit Search. Top Solutions. Manuals, documents, and other information for your product are included in this section. The first number in the bugcheck parens is the number of the trap (8 = double fault, etc) Consult an Intel x86 family manual to learn more about what these traps are.0x00000008, or Double Fault, indicates that an exception occurs during a call to the handler for a prior exception.
APPLICATION READY NETWORK GUIDE
MICROSOFT WINDOWS SERVER 2008
Comprehensive Application Ready infrastructure that enhances the security, availability, and performance of Microsoft Windows Server 2008 deployments
SUMMARY
Microsoft® Windows® Server 2008 is much more than just a new release from Microsoft. From a next generation TCP/IP stack to new versions of Windows Terminal Services and Internet Information services, as well as new technologies like Windows PowerShell and Secure Socket Tunneling Protocol, Windows Server 2008 helps information technology professionals maximize control over their infrastructure while providing unprecedented availability and management capabilities. F5 has worked with Microsoft during the beta cycle and beyond to ensure a high level of interoperability and optimization with the entire Windows Server 2008 platform. F5’s Application Ready Network for Windows Server 2008 not only helps optimize end-to-end performance, availability, and scalability
for Windows Server 2008 deployments, but reduces the costs associated with deployment, management, and operation.
F5 APPLICATION READY NETWORK GUIDE: MICROSOFT WINDOWS SERVER 2008
User Experience and
Application Performance
Microsoft Windows Server 2008 gives organizations a powerful new platform that is designed to power the next-generation of networks, applications, and Web services. Windows Server 2008 includes some exciting new components such as Microsoft’s new
TCP/IP stack, Secure Socket Tunneling Protocol (SSTP), and new versions of industry standard applications like Windows Terminal Services and Internet Information Services. F5 has been working closely with Microsoft to ensure that F5’s Application Ready Network for Microsoft Windows Server 2008 provides the highest level of application availability, performance, and end user satisfaction.
One of the highlights of Microsoft Windows Server 2008 is a next generation TCP/IP stack that has been completely redesigned from the ground up. F5 solutions include a host of TCP/IP optimization technologies that are
compatible with Microsoft’s new stack. These optimizations, which combine session-level application awareness, persistent tunnels, selective acknowledgements, error correction, and optimized TCP windows, enable F5 devices and Microsoft Server 2008 installations to fully utilize available bandwidth. This enables F5 devices to adapt, in real time, to the latency, packet loss, and congestion characteristics
of WAN links, and accelerate virtually all application traffic. And F5 isolates, controls, and independently optimizes user and server connections, enabling both the server and end user to maximize productivity.
With the rapid expansion of the Internet and the quickly diminishing number of IPv4
addresses available, organizations are looking to ensure their network infrastructure is adequately prepared for the future. Internet Protocol version 6 (IPv6) support is no longer a luxury, it is a necessity. IPv6, a new suite
of standard protocols for the network layer of the Internet, is built into both Windows Server 2008, as well as F5 devices, ensuring that your network and Microsoft applications
are ready for this inevitable change. With F5’s IPv6 support, organizations have a clear strategy for staging network migration as IPv6 traffic grows, without wholesale network and application upgrades. Additionally, F5 devices can perform IPv6/IPv4 translation, translating traffic for consumption by either IPv4 or IPv6 end points. This allows organizations to stage their migration gradually as demand for IPv6 increases. F5 enables you to freely intermingle IPv4 and IPv6 services on Windows Server 2008; for example, F5 can serve as an IPv4 front end to Windows Server 2008 Web Access servers that only use IPv6. With F5, organizations have a strong solution for today and well into the future.
Windows Server 2008 is extremely effective at what it was designed to do: provide a solid
foundation for server workload and application requirements. One of F5’s core strengths is the ability to enhance end-user experience while increasing application and server performance. We do this by taking on many of the duties that servers traditionally have to perform. If each server has to carry out processor-intensive tasks such as compression, caching, and SSL processing and certificate management, the amount of processing power these devices have left to perform core tasks is reduced.
By offloading these types of tasks onto F5’s centralized and high powered network devices, F5 greatly improves Windows Server 2008 server efficiency and enables organizations to reduce the amount of hardware. This applies to all the major components of Windows Server 2008, including Windows Terminal Services, Internet Information Servers, and SSTP.
F5 provides technology that guarantees the most efficient network possible. Because F5’s unique TMOS™ operating system is a full proxy, it can optimize any end point that connects through the system. As a full broker of communications, the system optimizes communication for every single end-device communicating through it. This optimization can take place up and down the entire stack
— from the transport layer to the protocol and application layer — functions outside the
control of Windows Server 2008. This takes the workload off of the Windows Server 2008 devices for increased server efficiency. By reducing unnecessary protocol communication across the network, F5 improves application response times and utilization for Windows Server 2008 deployments and other applications on the network.
Even high-powered and efficient applications and servers, like Windows Server 2008, as well as other devices on the local area network (LAN), are not much help over the wide area network (WAN). Network latency across the WAN is one of the biggest challenges facing IT departments around the world, and is a major concern for organizations deploying applications like Windows Terminal Services where users can access applications from anywhere. Simply increasing bandwidth
does nothing to solve the problem. F5 helps drastically reduce the impact of latency in a number of ways. In addition to the benefits from TMOS, F5 solves latency problems with a group of capabilities that eliminates the need for the browser to download repetitive or duplicate data, as well as ensuring the best use of bandwidth by controlling browser behavior. By reducing the extra conditional requests and excess data (re)transmitted between the
“Windows Server is one of the most popular application platforms that we see within our enterprise customer base. As such, F5 has put substantial resources into testing its application delivery portfolio with the Windows Server platform technologies through every step of the beta to maintain a high level of interoperability.”
Jim Ritchings, VP of Business
Development at F5
F5 APPLICATION READY NETWORK GUIDE: MICROSOFT WINDOWS SERVER 2008
browser and the web application, F5 mitigates the effects of WAN latency, networking errors, and packet loss.
One of the strengths of the F5’s Application Ready Network is the wide variety of materials that ease the burden of configuring and optimizing our devices, freeing valuable IT resources to work on other projects. As part of the Application Ready Network for Microsoft Windows 2008, F5 has configured, tested, and tuned our devices with the major components of Windows Server 2008 and carefully documented the procedures in our Deployment Guide. F5 also provides configuration Profiles and Policies to make configuration incredibly simple yet powerful and flexible, with some policies including prebuilt drop-downs for components like Microsoft Internet Information Services and Windows Terminal Services.
And now with our management devices, the deployment guide configuration files are available as a template, which can be easily
uploaded and pushed to F5 devices. With the power of Microsoft PowerShell, the command line shell and scripting language included with Windows Server 2008, and F5’s iControl PowerShell Cmdlets and scripts, developers have a unique way to control and manage F5 devices in one location1.
Application Security
While performance and end-user experience are vital to a successful deployment of Windows Server 2008, ensuring application security
can be even more crucial. Because of the sensitive nature of data stored in applications and databases, coupled with new compliance initiatives and government regulations on data protection, securing your applications is more important than ever before. F5 security solutions provide comprehensive protection for Windows Server 2008, ensuring your data and applications are secure.
Years ago, merely having network firewalls in front of the LAN was considered an adequate level of security. Next came intrusion protection/ detection systems, which added another level of security, albeit one that provided a negative
security model. However, IPS/IDS systems could only protect against a known list of attacks and signatures, and soon attacks became more sophisticated, with zero-day attacks that would bypass these systems as their signatures were previously unknown. Recently, hackers are shifting their focus to applications themselves
with attacks that look harmless to both network firewalls and intrusion protection/detection systems. More than 50 percent of all new vulnerabilities being identified on a weekly basis are attributed to web applications2.. Devices relying solely on a known list of signature attacks cannot defend against targeted attacks involving a malicious user seeking vulnerabilities unique to a particular application. F5 detects and mitigates patternless exploits in real time, adding accurate, complementary protection to existing firewalls and IDS devices, which do not efficiently address HTTP and HTTPS-borne threats.
In addition to analyzing and blocking known attack signatures, F5 can strip out identifying operating system and web server information (such as version strings, signatures, and fingerprinting) from message headers, conceal any HTTP error messages from users, and remove application error messages from pages sent to users while checking to ensure no server code or private HTML comments leak onto public web pages.
And attacks do not always come from the outside of the network; internal users can gain sensitive information or sabotage applications with greater ease than external users. Because F5 devices can offload SSL encryption duties, organizations can encrypt traffic for entire transactions, without affecting performance for the end user. This prevents information from being sent in clear text over the internal network, mitigating risks associated with internal users
as well as complying with state and federal regulations related to privacy.
F5 devices also protect against attacks that use cookies and other tokens that are transparently distributed for their entry point. F5 devices can be easily configured to encrypt cookies used by Windows Server 2008, preventing cookie tampering and other cookie-based attacks. This gives organizations superior security for all
stateful applications and a higher level of user identity trust.
F5 includes extremely granular endpoint security for remote users connecting to the network and to Windows Server 2008 servers and applications. Before a remote user can even
log on to the F5 devices to gain access to the network, F5 can determine if an antivirus or personal firewall is running on their PC and if it is up-to-date, or enforce a specific operating system patch level, among a host of other pre-logon checks. F5 can direct the user to a remediation page for further instructions or even turn on antivirus or firewalls for the user. F5 remote access also supports two-factor authentication from leading vendors for those organizations that require more than just a user name and password for access to the network. And F5’s remote access solution can be easily integrated with Active Directory, providing centralized authentication.
When the remote user is finished working with their remote access session, F5 includes a cache cleanup control that removes cookies, browser history, auto-complete information, browser cache, temp files, and all ActiveX controls installed during the remote access session from the client PC. This makes ensures that no information is left behind, which is critical for users connecting from public computers, such as a kiosk.
Not only does F5 provide comprehensive application security, but we produce extremely secure devices. We ensure your Windows Server 2008 deployment, and the information it contains, remains completely secure.
Unified Security Enforcement
and Access Control
Another integral piece of a complete security platform is security enforcement and access control. The number of employees requiring access to corporate resources from outside the network is growing every year. And it’s not only employees who need access to the network. With more business-to-business
1 For more information on iControl and Microsoft PowerShell integration, see http://devcentral.f5.com/Default.aspx?tabid=71
2 SANS@RISK, “The Consensus Security Vulnerability Report”
4
F5 APPLICATION READY NETWORK GUIDE: MICROSOFT WINDOWS SERVER 2008
transactions, and partners, contractors, and suppliers all clamoring for access to different internal applications, organizations are struggling with access control and enforcement issues.
F5 provides a complete approach to security enforcement and providing access control for Windows Server 2008, regardless of end user, client type, application, access network, or network resources.
In the past, remote access was provided by IPsec VPN solutions — a complicated deployment which required software installation and maintenance on every client, and was difficult to enforce and control. IPSec has shown it is unable to keep up with the growing demands of remote access required by today’s enterprise organizations. F5’s remote access solution enables you to easily grant remote access to anyone from any device, while ensuring this access is carefully controlled and restricted on a granular basis.
With F5, access to Windows Server 2008 resources can be easily controlled on an extremely granular level. For example, employees can be granted full access to internal resources, while a trusted partner group can be restricted to a specific subset of applications, and a contractor group could be locked down to a specific application or port. F5 centralizes this access control, and makes configuring and enforcing this type of control simple. F5 can even gather device information (like IP address or time of day) and determine if a resource should be offered. The F5 solution also includes control
for any access network and any device, with no need to deploy multiple access control solutions for remote users, wireless LANs, and the LAN.
F5 supports virtual administration domains, allowing a single F5 device to be managed by multiple application teams without interference. Every user can be assigned to specific administrative domains which define which objects are visible to that user. Multiple levels of access are also definable for each user, with basic read-only users who can log on to the devices to monitor status of specific objects and traffic quantities to full administrative users capable of making configuration changes to every object on the device. This increases productivity by reducing the time spent in meetings, tracking
down appropriate administrative personnel, and improves the ability of application administrations to manage applications when it’s necessary. F5 helps streamline the business process and improve the productivity and efficiency of operational personnel.
Business Continuity and
Disaster Recovery
Disaster recovery and business continuity are vital to the success of an organization. Merely having a solid security platform cannot protect against unexpected events and disasters that create a wide range of obstacles, ranging from knocking out the power to wiping out entire data centers. These disruptive events not only cost organizations thousands or even millions of dollars, but can bring about legal ramifications with industry and government rules concerning data protection and disaster recovery. With
the amount of irreplaceable, business critical information stored on the network and in applications like those found in Windows Server 2008, having an effective disaster recovery plan is essential.
F5 products are uniquely positioned to help organizations mitigate disasters and other disruptive events. F5 is the only vendor
to virtualize data centers, VPN access, optimization, and traffic in an integrated fashion — ensuring the Windows Server 2008 devices and applications are always available.
F5 provides the industry’s most comprehensive solution for site failover and business continuity. From performing comprehensive site application availability checks, to defining the conditions for dynamically and transparently shifting all traffic to a backup data center, failing over
an entire site, or controlling only the affected applications, F5 has the complete solution.
When one of these disruptive events does happen, even something as simple as a snow storm that prevents most employees from making it to the office, F5 provides extremely secure remote access to the network and Windows Server 2008 deployment, ensuring that even though the physical office might be unavailable, as long as a single data center
is still up, business can continue. F5 remote access devices support Microsoft Vista and access to Windows Server 2008 devices, and even provide secure application access from Windows Mobile® 5/6 PocketPC and Smartphones.
One scenario often neglected in a disaster recovery plan is when the event doesn’t happen to your organization, but to your ISP. While many organizations do have multiple links, they have to contend with complicated BGP configurations. F5 simplifies multi-homed deployments so you no longer need ISP cooperation, designated IP address blocks, ASNs, or reliance on complex BGP
configurations to protect your network from ISP failures. With F5 technology, an organization also has the choice of aggregating multiple small connections together rather than having to invest in a single high bandwidth connection. This frees businesses to expand their service
as they grow. F5 seamlessly monitors availability and performance of multiple WAN ISP connections to intelligently manage bi-directional traffic flows to a site, providing fault tolerant and optimized Internet access.
F5 devices detect errors across an entire link to provide end-to-end, reliable WAN connectivity. F5 monitors the health and availability of each connection, detecting outages to a link or ISP.
In the event of a failure, traffic is dynamically directed across other available links so users stay connected.
F5 APPLICATION READY NETWORK GUIDE: MICROSOFT WINDOWS SERVER 2008
Global F5 and Windows Server 2008 Deployment
The following example shows a global configuration, using the F5 suite of products to optimize, secure, and deliver Windows Server 2008 installations over the WAN and LAN.
Routers
WANJet 500
WANJet 500 | WANJet |
Enterprise Manager | |
BIG-IP | |
DMZ | Link Controller |
Firewalls |
FirePass |
BIG-IP
Global Traffic Manager
BIG-IP Application | |
Security Manager | |
WANJet 500 | BIG-IP |
Local Traffic Manager | |
WebAccelerator |
WTS 2008 | IIS 7.0 Windows Server |
2008 |
F5 TMOS
Headquarters
F5 TMOS
Branch Office
FirePass
WANJet
Remote Users
Internet or WAN
Routers | |
WANJet | Disaster |
Recovery Site | |
BIG-IP | |
DMZ | Link Controller |
FirePass | Firewalls |
BIG-IP | |
Global Traffic Manager | |
BIG-IP | |
Local Traffic Manager |
6
F5 APPLICATION READY NETWORK GUIDE: MICROSOFT WINDOWS SERVER 2008
Deployment Guides
Deploying the BIG-IP System with Microsoft Internet Information Services 7.0
Provides detailed procedures on how to configure the BIG-IP® Local Traffic Manager™ (LTM) and WebAccelerator™ with Internet Information Services 7.0.
Deploying the BIG-IP System with Microsoft Windows Server 2008 Terminal Services
Provides detailed procedures on how to configure the BIG-IP LTM with the new version of Windows Terminal Services.
See the Deployment Guide index on the F5 Solution Center for more Microsoft Guides.
For more information about the partnership between F5 and Microsoft, see the Microsoft Partner Showcase on the F5 Solution Center.
F5 Product offerings
BIG-IP Product Family
The BIG-IP products deliver high availability, improved performance, application security, and access control, all in one unit. A single BIG-IP device can do the work of a dozen single-purpose products. More importantly, it can do that work in an efficient, cohesive manner that is easier to manage and adapt as business and technology needs change.
Product Modules (These modules can also be run as standalone appliances)
LTM: The BIG-IP LTM allows organizations to ensure quality of service and manageability, apply business policies and rules to content delivery, support increasing traffic volumes, deliver their applications securely, enjoy operational efficiency and cost control,
and remain flexible to future application and infrastructure changes to protect their investments.
GTM: The BIG-IP Global Traffic Manager™ (GTM) Module provides high availability, maximum performance and global management for applications running across multiple and globally dispersed data centers. Seamlessly virtualizes FirePass VPN to automatically provide always-on access control.

ASM: The Application Security Manager™ provides application layer protection from both targeted and generalized application attacks to ensure that applications are always available and performing optimally.
WA: F5 WebAccelerator™ is an advanced web application delivery solution that provides a series of intelligent technologies designed to overcome problems with browsers, web application platforms, and WAN latency issues which impact user performance.
LC: The BIG-IP Link Controller™ Module seamlessly monitors availability and performance of multiple WAN connections to intelligently manage bi-directional traffic flows to a site – providing fault tolerant, optimized Internet access.
Feature Modules: These are individual feature packs that can be added to a BIG-IP traffic management platform. The Feature Modules include the Message Security, Intelligent Compression, L7 Rate Shaping,
IPv6 Gateway, Advanced Client Authentication, SSL Acceleration, Fast Cache, and Advanced Routing Modules.
FirePass
F5’s FirePass® SSL VPN appliance provides secure access to corporate applications and data using a standard web browser. Delivering outstanding performance, scalability, ease-of-use, and end-point security, FirePass helps increase the productivity of those working from home or on the road while keeping corporate data secure.
WANJet
WANJet® is an appliance-based solution that delivers LAN-like application performance over the WAN. WANJet accelerates applications including: file transfer, e-mail, client-server applications, data replication, and others, resulting in predictable, fast performance for all WAN users.
Enterprise Manager
F5’s appliance-based Enterprise Manager ™gives you the power to centrally discover and maintain the F5 devices in your network. With Enterprise Manager, you can archive and
safeguard device configurations for contingency planning, Configure new devices from a central location without manually working on each device, easily and quickly roll-out software upgrades and security patches and much more.
F5 Acopia ARX
F5 Acopia™ award-winning intelligent file virtualization solutions decouple file access from physical file location. Our ARX® products integrate seamlessly into existing Network Attached Storage (NAS), Windows®, UNIX® and Linux environments. ARX devices provide industry-leading scalability, performance and reliability, and are specifically designed to meet the needs of enterprise storage environments.
iControl API
iControl® is F5’s SOAP API exposed on each BIG-IP LTM system. iControl enables automation between the application and the network, and gives organizations the power and flexibility
to ensure that applications and the network work together for increased reliability, security, and performance. F5’s developer community, DevCentral, has sample iControl applications and code. Visit the Microsoft page on DevCentral for Microsoft-specific forums and other useful information about F5 integration with Microsoft applications.
www.f5.com
© 2008 F5 Networks, Inc. All rights reserved. F5, F5 Networks, the F5 logo, BIG-IP, FirePass, Acopia, ARX, WANJet, WebAccelerator are trademarks or registered trademarks of F5 Networks, Inc.
in the U.S. and certain other countries. | 7 |
-->
Applies To: Windows Server 2016 Essentials, Windows Server 2012 R2 Essentials, Windows Server 2012 Essentials
The Users page of the Windows Server Essentials Dashboard centralizes information and tasks that help you manage the user accounts on your small business network. For an overview of the Users Dashboard, see Dashboard Overview.
Managing user accounts
The following topics provide information about how to use the Windows Server Essentials Dashboard to manage the user accounts on the server:
Add a user account
When you add a user account, the assigned user can log on to the network, and you can give the user permission to access network resources such as shared folders and the Remote Web Access site. Windows Server Essentials includes the Add a User Account Wizard that helps you:
Provide a name and password for the user account.
Define the account as either an administrator or as a standard user.
Select which shared folders the user account can access.
Specify if the user account has remote access to the network.
Select email options if applicable.
Assign a Microsoft Online Services account (referred to as an Office 365 account in Windows Server Essentials) if applicable.
Assign user groups ( Windows Server Essentials only).
Note
- Non-ASCII characters are not supported in Microsoft Azure Active Directory (Azure AD). Do not use any non-ASCII characters in your password, if your server is integrated with Azure AD.
- The email options are only available if you install an add-in that provides email service.
To add a user account
Open the Windows Server Essentials Dashboard.
On the navigation bar, click Users.
In the Users Tasks pane, click Add a user account. The Add a User Account Wizard appears.
Follow the instructions to complete the wizard.
Remove a user account
When you choose to remove a user account from the server, a wizard deletes the selected account. Because of this, you can no longer use the account to log on to the network or to access any of the network resources. As an option, you can also delete the files for the user account at the same time that you remove the account. If you do not want to permanently remove the user account, you can deactivate the user account instead to suspend access to network resources.
Important
If a user account has a Microsoft online account assigned, when you remove the user account, the online account also is removed from Microsoft Online Services, and the user's data, including email, is subject to data retention policies in Microsoft Online Services. If you want to retain user data for the online account, deactivate the user account instead of removing it. For more information, see Manage Online Accounts for Users.
To remove a user account
Open the Windows Server Essentials Dashboard.
On the navigation bar, click Users.
In the list of user accounts, select the user account that you want to remove.
In the <User Account> Tasks pane, click Remove the user account. The Delete a User Account Wizard appears.
On the Do you want to keep the files? page of the wizard, you can choose to delete the user's files, including File History backups and the redirected folder for the user account. To keep the user's files, leave the check box empty. After making your selection, click Next.
Click Delete account.
Note
After you remove a user account, the account no longer appears in the list of user accounts. If you chose to delete the files, the server permanently deletes the user's folder from the Users server folder and from the File History Backups server folder.
If you have an integrated email provider, the email account assigned to the user account will also be removed.
View user accounts
The Users section of the Windows Server Essentials Dashboard displays a list of network user accounts. The list also provides additional information about each account.
To view a list of user accounts
Open the Windows Server Essentials Dashboard.
On the main navigation bar, click Users.
The Dashboard displays a current list of user accounts.
To view or change properties for a user account
In the list of user accounts, select the account for which you want to view or change properties.
In the <User Account> Tasks pane, click View the account properties. The Properties page for the user account appears.
Click a tab to display the properties for that account feature.
To save any changes that you make to the user account properties, click Apply.
Change the display name for the user account
The display name is the name that appears in the Name column on the Users page of the Dashboard. Changing the display name does not change the logon or sign-in name for a user account.
To change the display name for a user account
Open the Windows Server Essentials Dashboard.
On the navigation bar, click Users.
In the list of user accounts, select the user account that you want to change.
In the <User Account> Tasks pane, click View the account properties. The Properties page for the user account appears.
On the General tab, type a new First name and Last name for the user account, and then click OK.
The new display name appears in the list of user accounts.
Activate a user account
When you activate a user account, the assigned user can log on to the network and access network resources to which the account has permission, such as shared folders and the Remote Web Access site.
Note
You can only activate a user account that is deactivated. You cannot activate a user account after you remove it from the server.
To activate a user account
Open the Windows Server Essentials Dashboard.
On the navigation bar, click Users.
In the list view, select the user account that you want to activate.
In the <User Account> Tasks pane, click Activate the user account.
In the confirmation window, click Yes to confirm your action.
Note
After you activate a user account, the status for the account displays Active. The user account regains the same access rights that were assigned prior to account deactivation.
If you have an integrated email provider, the email account assigned to the user account will also be activated.
Deactivate a user account
When you deactivate a user account, account access to the server is temporarily suspended. Because of this, the assigned user cannot use the account to access network resources such as shared folders or the Remote Web Access site until you activate the account.
If the user account has a Microsoft online account assigned, the online account is also deactivated. The user cannot use resources in Office 365 and other online services that you subscribe to, but the user's data, including email, is retained in Microsoft Online Services.
Note
You can only deactivate a user account that is currently active.
To deactivate a user account
Open the Windows Server Essentials Dashboard.
On the navigation bar, click Users.
In the list view, select the user account that you want to deactivate.
In the <User Account> Tasks pane, click Deactivate the user account.
In the confirmation window, click Yes to confirm your action.
Note
After you deactivate a user account, the status for the account displays Inactive.
If you have an integrated email provider, the email account assigned to the user account will also be deactivated.
Understand user accounts
A user account provides important information to Windows Server Essentials, which enables individuals to access information that is stored on the server, and makes it possible for individual users to create and manage their files and settings. Users can log on to any computer on the network if they have a Windows Server Essentials user account and they have permissions to access a computer. Users access their user accounts with their user name and password.
There are two main types of user accounts. Each type gives users a different level of control over the computer:
Standard accounts are for everyday computing. The standard account helps protect your network by preventing users from making changes that affect other users, such as deleting files or changing network settings.
Administrator accounts provide the most control over a computer network. You should assign the administrator account type only when necessary.
Manage user accounts using the Dashboard
Windows Server Essentials makes it possible to perform common administrative tasks by using the Windows Server Essentials Dashboard. By default, the Users page of the Dashboard includes two tabs: Users and Users Groups.
Note
- If you integrate your server that is running Windows Server Essentials with Office 365, a new tab called Distribution Groups is also added within the Users page of the Dashboard.
- In Windows Server Essentials, the Users page of the Dashboard includes only a single tab - Users.
The Users tab includes the following:
A list of user accounts, which displays:
The name of the user.
The Logon name for the user account.
Whether the user account has Anywhere Access permission. Anywhere Access permission for a user account is either Allowed or Not allowed.
Whether the File History for this user account is managed by the server running Windows Server Essentials. The File History status for a user account is either Managed or Not managed.
The level of access that is assigned to the user account. You can assign either Standard user access or Administrator access for a user account.
The user account status. A user account can be Active, Inactive, or Incomplete.
In Windows Server Essentials, if the server is integrated with Office 365 or Windows Intune, the Microsoft online account is displayed.
In Windows Server Essentials, if the server is integrated with Microsoft Office 365, the status of the Office 365 account (known in Windows Server Essentials as the Microsoft online account) for the user account is displayed.
A details pane with additional information about a selected user account.
A tasks pane that includes:
A set of user account administrative tasks such as viewing and removing user accounts, and changing passwords.
Tasks that allow you to globally set or change settings for all user accounts in the network.
The following table describes the various user account tasks that are available from the Users tab. Some of the tasks are user account-specific, and they are only visible when you select a user account in the list.
Note
If you integrate Office 365 with Windows Server Essentials, additional tasks will become available. For more information, see Manage Online Accounts for Users.
User account tasks in the Dashboard
| Task name | Description |
|---|---|
| View the account properties | Enables you to view and change the properties of the selected user account, and to specify folder access permissions for the account. |
| Deactivate the user account | A user account that is deactivated cannot log on to the network or access network resources such as shared folders or printers. |
| Activate the user account | A user account that is activated can log on to the network and can access network resources as defined by the account permissions. |
| Remove the user account | Enables you to remove the selected user account. |
| Change the user account password | Enables you to reset the network password for the selected user account. |
| Add a user account | Starts the Add a User Account Wizard, which enables you to create a single new user account that has either standard user access or administrator access. |
| Assign a Microsoft online account | Adds a Microsoft online account to the local network user account that is selected. This task is displayed when your server is integrated with Microsoft online services, such as Office 365. |
| Add Microsoft online accounts | Adds Microsoft online accounts and associates them to local network user accounts. This task is displayed when your server is integrated with Microsoft online services, such as Office 365. |
| Set the password policy | Enables you to change the values of the password polices for your network. |
| Import Microsoft online accounts | Performs a bulk import of accounts from Microsoft online services into the local network. This task is displayed when your server is integrated with Microsoft online services, such as Office 365. |
| Refresh | Refreshes the Users tab. This task is applicable to Windows Server Essentials. |
| Change File History settings | Enables you to change File History settings, such as backup frequency, or backup duration. This task is applicable to Windows Server Essentials. |
| Export all remote connections | Creates a .CSV-format file of all remote connections to the server that have occurred over the past 30 days. |
Managing passwords and access
The following topics provide information about how to use the Windows Server Essentials Dashboard to manage user account passwords and user access to the shared folders on the server:
Change or reset the password for a user account
To change or reset a user account password, follow these steps.
To reset the password for a user account
Open the Windows Server Essentials Dashboard.
On the navigation bar, click Users.
In the list of user accounts, select the user account that you want to reset.
In the <User Account> Tasks pane, click Change the user account password. The Change User Account Password Wizard appears.
Type a new password for the user account, and then type the password again to confirm it.
Click Change password.
Provide the new password to the user.
Important
- You may not be able to change your password if the password policy for your account has been set to Passwords never expire.
- Non-ASCII characters are not supported in Azure AD. Therefore, if your server is integrated with Azure AD, do not use any non-ASCII characters in your password.
- If a Microsoft online account (known in Windows Server Essentials as an Office 365 account) is assigned to the user, the password is synchronized with the online account password. The user will use the new password to sign in on the server or sign in to Office 365. For more information, see Manage Online Accounts for Users.
- You may not be able to change your password if the password policy for your account has been set to Passwords never expire.
What you should know about password policies
The password policy is a set of rules that define how users create and use passwords. The policy helps to prevent unauthorized access to user data and other information that is stored on the server. The password policy is applied to all user accounts that access the network.
The Windows Server Essentials password policy consists of three primary elements as follows:
Password length. The longer a password is, the more secure it is. Blank passwords are not secure.
Password complexity. Complex passwords contain a mixture of uppercase and lowercase letters (a-z, A-Z), base numbers (0-9), and non-alphabetic symbols (such as; !,@,#,_,-). Complex passwords are much less susceptible to unauthorized access. Passwords that contain user names, birthdates, or other personal information do not provide adequate security.
Password age. Windows Server Essentials requires that users change their password at least once every 180 days. As an option, you can choose to have passwords never expire.
To make it easier to implement a password policy on your computer network, Windows Server Essentials provides a simple tool that allows you to set or change the password policy to any of the following four pre-defined policy profiles:
Weak. Users can specify any password that is not blank.
Medium. These passwords must contain at least 5 characters. A complex password is not required.
Medium Strong. These passwords must contain at least 5 characters, and must include letters, numbers, and symbols.
Strong. These passwords must contain at least 7 characters, and must include letters, numbers, and symbols. These passwords are more secure, but may be more difficult for users to remember.
Note
Passwords cannot contain the user name or email address.
If you integrate with Office 365, the integration enforces the Strong password policy, and updates the policy to include the following requirements:
- Passwords must contain 8 �16 characters.
- Passwords cannot contain a space or the Office 365 email name.
By default, server installation sets the default password policy to the Strong option.
- Passwords must contain 8 �16 characters.
Change the password policy
Use the following procedure to set or change the password policy to any of four pre-defined policy profiles.
To change the password policy
Open the Windows Server Essentials Dashboard, and then click Users.
In the Users Tasks pane, click Set the password policy.
On the Change the Password Policy screen, set the level of password strength by moving the slider.
Microsoft recommends that you set the password strength to Strong.
Note
As an option, you can also select Passwords never expire. This setting is less secure, and so it is not recommended.
Click Change policy.
Level of access to shared folders
As a best practice, you should assign the most restrictive permissions available that still allow users to perform required tasks.
You have three access settings available for the shared folders on the server:
Read/Write. Choose this setting if you want to allow the user account permission to create, change, and delete any files in the shared folder.
Read only. Choose this setting if you want to allow the user account permission to only read the files in the shared folder. User accounts with read-only access cannot create, change, or delete any files in the shared folder.
No access. Choose this setting if you do not want the user account to access any files in the shared folder.
Retain and manage access to files for removed user accounts
Windows Server 2008 R2 Features
The network administrator can remove a user account and choose to keep the user's files for future use. In this scenario, the removed user account can no longer be used to sign in to the network; however, the files for this user will be saved in a shared folder, which can be shared with another user.
Important
Be aware that if you remove a user account that has a Microsoft online account assigned, the online account is also removed, and the user data, including email, is subject to data retention policies in Microsoft Online Services. To retain the user data for the online account, deactivate the user account instead of removing it. For more information, see Manage Online Accounts for Users.
To remove a user account but retain access to the user's files
Open the Windows Server Essentials Dashboard.
On the navigation bar, click Users.
In the list of user accounts, select the user account that you want to remove.
In the <User Account> Tasks pane, click Remove the user account. The Delete a User Account Wizard appears.
On the Do you want to keep the files? page, make sure that the Delete the files including File History backups and redirected folder for this user account check box is clear, and then click Next.
A confirmation page appears warning you that are deleting the account but keeping the files.
Click Delete account to remove the user account.
After the user account is removed, the administrator can give another user account access to the shared folder.
To give a user account permission to access a shared folder
Open the Windows Server Essentials Dashboard.
On the navigation bar, click Storage, and then click the Server Folders tab.
In the list of folders, select the Users folder.
In the Users Tasks pane, click Open the folder. Windows Explorer opens and displays the contents of the Users folder.
Right-click the folder for the user account that you want to share, and then click Properties.
In <User Account> Properties, click the Sharing tab, and then click Share.
In the File Sharing window, type or select the user account name with whom you want to share the folder, and then click Add.
Choose the Permission Level that you want the user account to have, and then click Share.
Synchronize the DSRM password with the network administrator password
Download Windows Server 2008 R2
Directory Services Restore Mode (DSRM) is a special boot mode for repairing or recovering Active Directory. The operating system uses DSRM to log on to the computer if Active Directory fails or needs to be restored. If your network administrator password and the DSRM password are different, DSRM will not load.
During a clean, first-time installation of Windows Server Essentials, the program sets the DSRM password to the network administrator account password that you specify during setup or in the migration answer file. When you change your network administrator password (as recommended typically every 60 days for increased server security), the password change is not forwarded to DSRM. This results in a password mismatch. If this occurs, you can use the following solutions to manually or automatically synchronize your network administrator's password with the DSRM password.
To manually synchronize the DSRM password to a network administrator account
At a command prompt, run
ntdsutil.exeto open the ntdsutil tool.To reset the DSRM password, type set dsrm password.
To synchronize the DSRM password on a domain controller with the current network administrator's account, type:
sync from domain account<current_network_administrator_account>, and then press Enter.
Because you will periodically change the password for the network administrator account, to ensure that the DSRM password is always the same as the current password of the network administrator, we recommend that you create a schedule task to automatically synchronize the DSRM password to the network administrator password daily.
To automatically synchronize the DSRM password to a network administrator account
From the server, open Administrative Tools, and then double-click Task Scheduler.
In the Task Scheduler Actions pane, click Create Task.
In the Name text box, type a name for the task such as AutoSync DSRM Password, and then select the Run with highest privileges option.
Define when the task should run:
In the Create Task dialog box, click the Triggers tab, and then click New.
In the New Trigger dialog box, select your recurrence option, specify the recurrence interval, and choose a start time.
Note
As a best practice, you should set the task to run daily during non-business hours.
Click OK to save your changes and return to the Create Task dialog box.
Define the task actions:
Click the Actions tab, and then click New. The New Action dialog box appears.
In the Action list, click Start a program, and then browse to C:WINDOWSSYSTEM32ntdsutil.exe.
In the Add arguments(optional) text box, type the following (you must include the quotation marks): set dsrm password sync from domain account SBS_network_administrator_account q q where SBS_network_administrator_account is the current network administrator's account name.
Click OK twice to save the task and close the Create Task dialog box. The new task appears in the Active Tasks section of Task Schedule.
Give user accounts remote desktop permission
In the default installation of Windows Server Essentials, network users do not have permission to establish a remote connection to computers or other resources on the network.
Before network users can establish a remote connection to network resources, you must first set up Anywhere Access. After you set up Anywhere Access, users can access files, applications, and computers in your office network from a device in any location with an Internet connection.
The Set up Anywhere Access Wizard allows you to enable two methods of remote access:
Virtual private network (VPN)
Remote Web Access
When you run the wizard, you can also choose to allow Anywhere Access for all current and newly added user accounts.
To set up Anywhere Access, open the Dashboard Home page, click SETUP, and then click Set up Anywhere Access.
For more information about Anywhere Access, see Manage Anywhere Access.
Enable users to access resources on the server
This section applies to a server running Windows Server Essentials or Windows Server Essentials, or to a server running Windows Server 2012 R2 Standard or Windows Server 2012 R2 Datacenter with the Windows Server Essentials Experience role installed.
If you want users to use remote access, and/or have individual user accounts, after you finish connecting a computer to the server, you can create new network user accounts for the users of the networked computer on the server by using the Dashboard. For more information about creating a user account, see Add a user account. After creating the user accounts, you must provide the network user name and password information to the users of the client computer so that they can access resources on the server by using the Launchpad.
For each user account that you create you can set access for the following through the user account properties:
Shared folders. By default, network administrators have Read/Write permission to all the shared folders, and standard user accounts have Read-only permissions to the Company folder. If media streaming is enabled, you can assign folder access permissions for individual standard user accounts for the following shared folders: Music, Pictures, Recorded TV, and Videos. You can set permissions for user accounts to access shared folders on the Shared folders tab of the user account properties.
Anywhere Access. By default, network administrators can use either VPN or Remote Web Access to access server resources. For standard user accounts, you must set user account permissions on the Anywhere Access tab.
Computer access. By default, network administrators can access all the computers in the network. However, for standard user accounts you can set individual user account permissions for accessing computers on the network on the Computer access tab of the user account properties.
To edit user account properties in Windows Server Essentials 2012 R2
Open the Windows Server Essentials Dashboard.
On the navigation bar, click USERS.
In the list of user accounts, select the user account that you want to edit.
In the <User Account> Tasks pane, click View the account properties.
In the <User Account> Properties, do the following:
On the Shared folders tab, set the appropriate folder permissions for each shared folder as needed.
On the Anywhere Access tab:
To allow a user to connect to the server by using VPN, select the Allow Virtual Private Network (VPN) check box.
To allow a user to connect to the server by using Remote Web Access, select the Allow Remote Web Access and access to web services applications check box.
On the Computer access tab, select the network computers that you would like the user to have access to.
To edit user account properties in Windows Server Essentials 2012
Open the Windows Server Essentials Dashboard.
On the navigation bar, click USERS.
In the list of user accounts, select the user account that you want to edit.
In the <User Account> Tasks pane, click Properties.
In the <User Account> Properties, do the following:
On the General tab, select User can view network health alerts if the user account needs to access network health reports.
On the Shared folders tab, set the appropriate folder permissions for each shared folder as needed.
On the Anywhere Access tab:
To allow a user to connect to the server by using VPN, select the Allow Virtual Private Network (VPN) check box.
To allow a user to connect to the server by using Remote Web Access, select the Allow Remote Web Access and access to web services applications check box.
On the Computer access tab, select the network computers that you would like the user to have access to.
Change remote access permissions for a user account
A user can access resources located on the server from a remote location by using a virtual private network (VPN), Remote Web Access, or other web services applications. By default, remote access permissions are turned on for network users when you configure Anywhere Access in Windows Server Essentials by using the Dashboard.
To change remote access permissions for a user account
Open the Windows Server Essentials Dashboard.
On the navigation bar, click Users.
In the list of user accounts, select the user account that you want to change.
In the <User Account> Tasks pane, click View the account properties. The Properties page for the user account appears.
On the Anywhere Access tab, do the following:
Select the Allow Virtual Private Network (VPN) check box to allow a user to connect to the server by using VPN.
Select the Allow Remote Web Access and access to web services applications check box to allow a user to connect to the server by using Remote Web Access.
Click Apply, and then click OK.
Change virtual private network permissions for a user account
You can use a virtual private network (VPN) to connect to Windows Server Essentials and access all your resources that are stored on the server. This is especially useful if you have a client computer that is set up with network accounts that can be used to connect to a hosted Windows Server Essentials server through a VPN connection. All the newly created user accounts on the hosted Windows Server Essentials server must use VPN to log on to the client computer for the first time.
To change VPN permissions for network users
Open the Windows Server Essentials Dashboard.
On the navigation bar, click USERS.
In the list of user accounts, select the user account to which you want to grant permissions to access the desktop remotely.
In the <User Account> Tasks pane, click Properties.
In the <User Account> Properties, click the Anywhere Access tab.
On the Anywhere Access tab, to allow a user to connect to the server by using VPN, select the Allow Virtual Private Network (VPN) check box.
Click Apply, and then click OK.
Change access to internal shared folders for a user account
Windows Server 2008 R2 Standard
You can manage access to any shared folders on the server by using the tasks on the Server Folders tab of the Dashboard. By default, the following server folders are created when you install Windows Server Essentials:
Client Computer Backups. Used to store client computer backups created by Windows Server backup. This server folder is not shared.
Company. Used to store and access documents related to your organization by network users.
File History Backups. By default, Windows Server Essentials stores file backups created by using File History. This server folder is not shared.
Folder Redirection. Used to store and access folders that are set up for folder redirection by network users. This server folder is not shared.
Music. Used to store and access music files by network users. This folder is created when you turn on media sharing.
Pictures. Used to store and access pictures by network users. This folder is created when you turn on media sharing.
Recorded TV. Used to store and access recorded TV programs by network users. This folder is created when you turn on media sharing.
Videos. Used to store and access videos by network users. This folder is created when you turn on media sharing.
Users. Used to store and access files by network users. A user-specific folder is automatically generated in the Users server folder for every network user account that you create.
To change access to a shared folder for a user account
Open the Windows Server Essentials Dashboard.
Click STORAGE, and then click Server Folders.
Navigate to and select the server folder for which you want to modify permissions.
In the task pane, click View the folder properties.
In <FolderName> Properties, click Sharing, and select the appropriate user access level for the listed user accounts, and then click Apply.
Note
You cannot modify the sharing permissions for File History Backups, Folder Redirection, and Users server folders. Hence, the folder properties of these server folders do not include a Sharing tab.
Allow user accounts to establish a remote desktop session to their computer
This section applies to a server running Windows Server Essentials or Windows Server Essentials, or to a server running Windows Server 2012 R2 Standard or Windows Server 2012 R2 Datacenter with the Windows Server Essentials Experience role installed.
The network administrator can grant permissions to network users that allow them to access their network computers from a remote location.
To enable users to access their network computers from a remote location
Open the Windows Server Essentials Dashboard.
On the navigation bar, click USERS.
In the list of user accounts, select the user account that you want to grant permissions for accessing the desktop remotely.
In the <User Account> Tasks pane, click Properties.
In the <User Account> Properties, click the Computer Access tab.
Select the computers that you want this user account to be able to access remotely, and then click OK.